Using client side certificates in WebDAV Nav+ iOS
WebDAV Nav+ includes some basic support for using client certificates when establishing an SSL connection to a server.
- WebDAV Nav+ expects the certificate to be in PKCS12 format, with a .p12 extension.
To create the certificate in the correct format from command line use a command like:openssl pkcs12 -export -in mycert.pem -inkey mykey.key\ -out demo.p12 -name "Demo Certificate" - Copy the file to the root folder (Documents) of the local storage, either by using iTunes File Sharing or downloading the file from a WebDAV server.
- The filename should be the same as the Name you've given the
server connection when adding the server to WebDAV Nav+
In this example the connection has been named "demo"
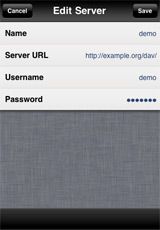
- When you attempt a connection from within WebDAV Nav+ the application will attempt to open the certificate file and prompt for a passphrase if required.
Generating self-signed certificates for testing
# Create the CA Key and Certificate openssl genrsa -des3 -out ca.key 4096 openssl req -new -x509 -days 365 -key ca.key -out ca.crt # Create the Server Key and CSR openssl genrsa -des3 -out server.key 1024 openssl req -new -key server.key -out server.csr # Sign server certificate openssl x509 -req -days 365 -in server.csr -CA ca.crt -CAkey ca.key -set_serial 01 -out server.crt # Create the Client Key and CSR openssl genrsa -des3 -out mycert.key 1024 openssl req -new -key mycert.key -out mycert.csr # Sign the client certificate with our CA cert. openssl x509 -req -days 365 -in mycert.csr -CA ca.crt -CAkey ca.key -set_serial 01 -out mycert.crt #Convert to the PKCS12 format required by WebDAV Nav openssl pkcs12 -export -in client.crt -inkey client.key -out demo.p12 -name "Demo Certificate"
Configure Apache to use the server and client certificates
SSLEngine on SSLCertificateFile /data/certs/server.crt SSLCertificateKeyFile /data/certs/server.key SSLCACertificateFile /data/certs/ca.crt SSLVerifyClient require SSLVerifyDepth 1